· 4 min read · Plaintext Version
how to ensure the safety of your applications with DevOps
When it comes to DevOps, security can't be an afterthought. Ensure that your systems and data are protected, and your organization can continue to innovate and thrive by integrating this thinking into the process from the very beginning.

Table of Contents
Key Takeaways
- Integrate security early by adding automated checks in your CI/CD pipeline.
- Train developers on secure coding and threat awareness to build safer apps.
- Centralize and encrypt configuration and secrets to protect sensitive data.
- Use strong access controls and frequent permission audits to prevent breaches.
- Always require multifactor authentication for accessing critical systems.
The following article is an except from my free ebook: Getting Started with DevOps.
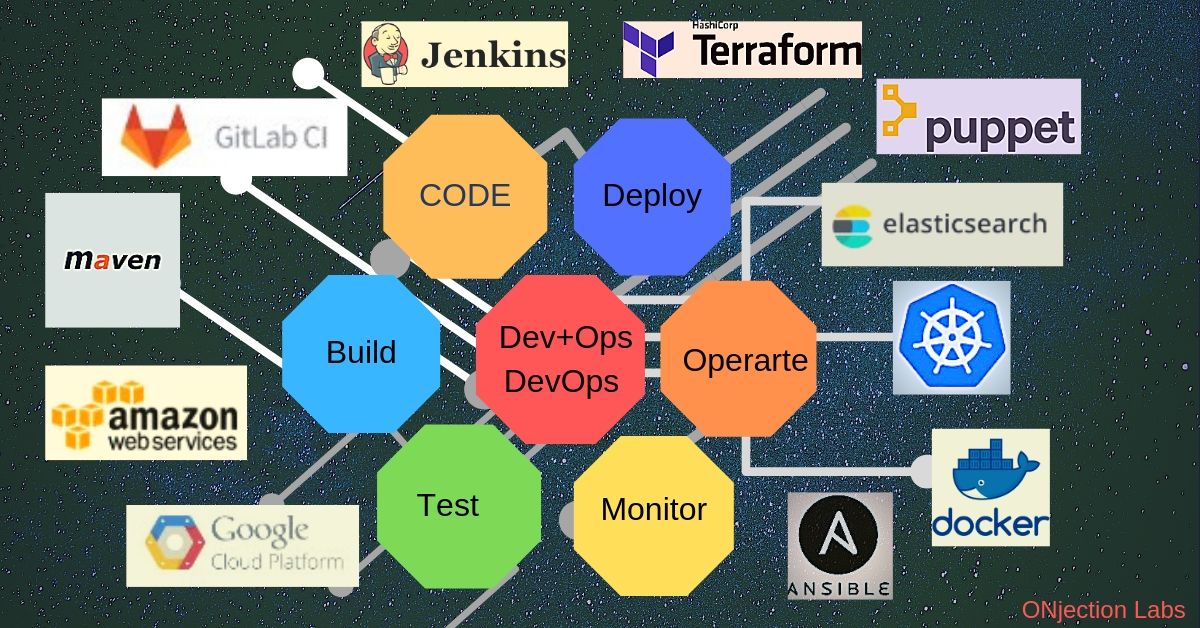
DevOps is all about streamlining the development and operations process to make it more efficient and faster. This means that teams are able to release new features and updates at a much quicker pace. However, with this speed comes the risk of security vulnerabilities being overlooked or ignored.
Think about it this way: if you’re moving quickly and not paying attention to security, it’s like driving a car without a seatbelt on. Sure, you may get to your destination faster, but if something goes wrong, the consequences can be severe. The same goes for DevOps - if security isn’t a priority, it can lead to major issues down the line.
With the rise of cloud computing and the internet of things, our systems and data are more connected than ever before. This means that a security breach in one area of your DevOps pipeline can have a ripple effect throughout the entire system. With Cloud and DevOps, the attack surface is becoming much larger and with the distributed nature of these systems, it is becoming more and more difficult to identify and protect against threats.
Shifting Left with Security
With a DevOps mindset, shifting left with your security considerations could be achieved by incorporating security into the continuous integration and continuous deployment (CI/CD) pipeline. This means including automated security testing as part of the build and deployment process, and also incorporating security considerations into the requirements and design phase of the development process. By doing this, teams can identify potential security issues early on and address them before they become major problems.
Implementing Secure Coding Practices
When it comes to implementing secure coding practices in a DevOps environment, one approach is to incorporate security training and education for developers. This can include things like training on secure coding practices, vulnerability management, and threat modelling. By upskilling and educating developers on these topics, you can help empower your teams to be security aware by default, ensuring that they are aware of potential security risks and know how to write code that is secure.
Securely managing configuration and secrets
Managing configuration and secrets is a critical part of effective software development, as it involves securely storing and managing sensitive information such as passwords, API keys, and certificates. If not done properly, it can lead to serious security breaches and data loss.
Configuration and secrets, such as passwords and API keys, are the keys to accessing sensitive information and systems. If they fall into the wrong hands, it can lead to serious security breaches and data loss. Additionally, hardcoding secrets into configuration files or applications can make them difficult to update or rotate, which can increase the risk of unauthorized access.
When you store all your secrets and configurations in one centralized location, it makes it much easier to apply security measures like encryption and access controls.
Managing Access and Permissions
Managing access and permissions is critical for ensuring the security of your systems and data in a DevOps environment. You should ensure that you have an effective and proven strategy for controlling who has access to sensitive data and systems in which context, as well as ensuring that only authorized personnel are able to access and make changes to your infrastructure.
Another important but often overlooked aspect of managing access and permissions is to require the use of multifactor authentication (MFA). This means that in addition to a username and password, additional forms of authentication should be required to access sensitive data and systems. This can include things like a security token or biometric authentication.
It is also important to regularly review and audit access and permissions to ensure that they are up-to-date, and that only authorized personnel have access to sensitive data and systems. Ideally, you should implement monitoring and logging of access to sensitive data and systems to identify any suspicious activity and take appropriate action if necessary.
Summary
When it comes to DevOps, security can’t be an afterthought. It needs to be integrated into the process from the very beginning. By understanding the importance of security in DevOps, you can ensure that your systems and data are protected, and your organization can continue to innovate and thrive.